Member-only story
Crimson — AppSec firearm III
Guidelines for the crimson_exploit module usage.

INTRODUCTION
This article will describe how to use the crimson_exploit most optimally.
The module is used for finding the vulnerabilities in many URLs.
The
crimson_exploitshould be used after the manual testing to ensure nothing was left out. The module is good at finding vulnerabilities with the GET method.
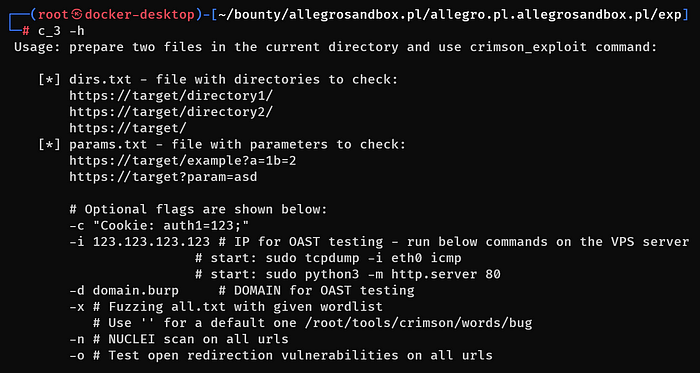
CRIMSON EXPLOIT GUIDELINES
You need the dirs.txt and params.txt directories to start using the third module. You can see an example content of the files on the screen above.
These two files are created in the
exp/directory after finishing the execution of the second module —crimson_target.
If you got the files in the current directory, you could start the tool by simply issuing the c_3 command. However, it is advised to use additional flags:

The module will stop and remind you to remove URLs you do not want to test.
OAST
-dflag stands for out-of-bound testing with a given collaborator domain.-iflag stands for out-of-bound testing with a given VPS IP address.
The flags are optional, but if you want to test the URLs with out-of-bound techniques, then both flags must be used at once to make the tool work properly.
The tool uses payloads that send the ICMP packets or TCP packets on port 80 when the payloads are triggered (if the potential vulnerabilities were found).
If you are using these flags, you need to start two listeners on your VPS:
FUZZING
-xflag stands for fuzzing. The empty value (‘’) instruct the module to use the default wordlist/root/tools/crimson/words/bug.
You can use your wordlist for fuzzing the URLs…