Member-only story
Crimson — AppSec firearm II
Guidelines for the crimson_target module usage.

INTRODUCTION
This article describes how to use the crimson_target most optimally.
The module is used for the single domain enumeration. It will:
- find the URLs corresponding to the targetted site
- check for vulnerabilities in the domain with different tools.
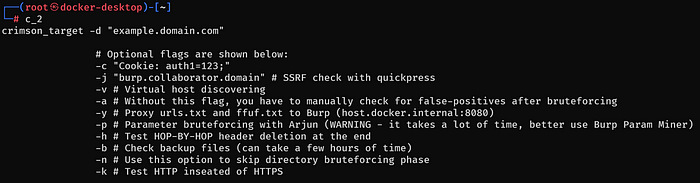
CRIMSON TARGET GUIDELINES
To begin, start the crimson_target against the chosen domain:
-jflag stands for SSRF check with quickpress use it with the Burp Collaborator domain as the argument — this flag is unnecessary.
You can run the module without
-jflag. It will just throw some errors if there is a WordPress instance running on the domain.
-vflag stands for virtual hosts discovery — this flag is not necessary.
The brute-forcing is carried by Wfuzz and it is taken against main domain.
For instance if you are targetingallegro.pl.allegrosandbox.plWfuzz will brute-forceFUZZ.allegrosandbox.plto find new virtual hostnames.
-ystands for proxying the findings (URLs) to the Burp Suite at the end of execution — this flag is not necessary.
Remember to turn on the Burp Suite, and turn off an interception:
-hflag stands for testing the HOP-BY-HOP header deletion at the end of the module execution — this flag is unnecessary.
It will check for this vulnerability only on the main page. It takes around 25 minutes to accomplish the scan. It is worth using it always.

There will be an error prompt from the CMSeek tool at startup, do not worry, it is just a message that there is no results directory. Press enter to continue.
- If you want to run a fully automated version of the crimson_target, you can use
-aflag, but I…